Wait, Don't Click That!
Written by: Venee Galloway, SBCS, CLCS, CBIA
With the COVID-19 epidemic sweeping across the globe, more and more businesses are using technology to carryout tasks. Aside from the increased use of web conferencing platforms and online adherence software, everyone is seeing an uptick in emails. Inboxes are now inundated with messages from vendors, clients and colleagues all sharing COVID-19 related information to help sustain your business during this time.
Unfortunately, hackers are taking advantage of the situation. There have been marked increases in the number of cyber attacks on US businesses. According to Evolve, a leading Cyber Liability managing general agent (MGA), over 4000 fraudulent domains containing the words “COVID and/or Corona” have been registered. These domains are, without a doubt, going to be used to execute phishing and ransomware attacks by posing as recognizable businesses and organizations.
On March 15, 2020 the US Department of Health and Human Services reported that a distributed denial of service (DDOS) attack had been leveled against their website. In Italy, the same type of attack took down their Social Security website preventing citizens from applying for their €600 relief payments. Now that we are aware of the increased potential for a breach, we want to help you to protect your systems and data from unauthorized capture.
Multi Factor Authentication – If you are not using MFA to secure your logins, then there is no time like the present. MFA adds an additional step to ensure that only authorized users are logging into your systems and applications. Many banks and social media sites have already implemented MFA, and we recommend doing the same wherever and whenever possible. Typically, once you have logged into an application with MFA, you will receive a text or email to a separate account with a validation code. That code is then entered into the application to confirm and grant access
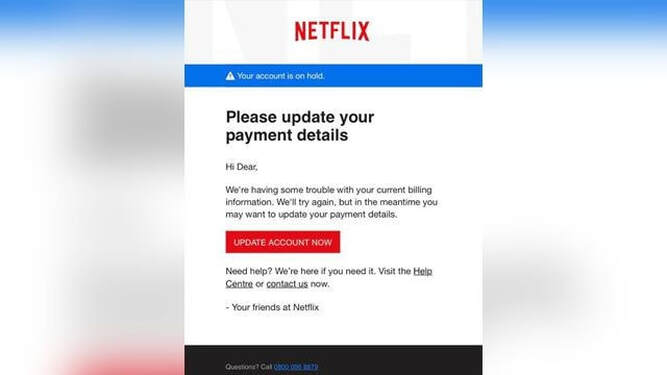
Phishing – Phishing is a way for hackers to infiltrate a network with fraudulent emails or text messages that appear to come from legitimate users. For example, you may get an email that appears to come from within your organization or from an existing vendor. Always be sure to trust your instincts. If something looks off, then it probably is. Before opening any attachments, always verify the sender by clicking their name to view the full email address. See the example below provided by FTC.gov:
This email looks legitimate at first glance, but, upon closer inspection, you will notice several things are off. Bad grammar and misspellings are often prevalent in Phishing emails or texts. Check to see if your name is missing or a generic greeting is used. Usually if you have an account, your name and account details will be included. In the example above, the scammer used the greeting, “Hi Dear” which should immediately tip off the receiver. Also pay attention to the contact listed, does it contains an email address suffix that is not common (.in, .com.co, etc.) or a phone number that is international? If so, chances are it is designed to be a scam. When in doubt, call and verify if the correspondence is legitimate using a number you have used previously or one located on the legitimate website.
Be Proactive – The best way to prevent a cyber attack is to be proactive. Make sure you change your passwords often and keep your system, antivirus and malware detection software up to date. If you receive a suspicious email, reach out to the sender to verify their identity BEFORE clicking on any links or attachments. Purchase a cyber liability policy and speak to your Agent about other cyber-crime coverages that may help you restore your service faster in the event of a breach.
Although some criminals are always looking to capitalize in a crisis current situation, we want you to know there are countless others who want to help. For more information on phishing and how to protect yourself from email scams, please review the link below from the Federal Trade Commission on “How to Recognize and Avoid Phishing Scams”: https://www.consumer.ftc.gov/articles/how-recognize-and-avoid-phishing-scams
.jpg)
Comments
Post a Comment